.svg)
.svg)
.svg)
.svg)
.svg)
Application Detection & Response
Stop attacks at the first malicious action
Kodem ADR uses Exploit Trigger Defense to identify and stop threats the moment they begin, before they become breaches. Most ADR tools detect symptoms. Kodem detects intent.

“Kodem ADR gives us signal, not noise. It detects the first function call in the exploit path, before damage happens. That precision lets our team move quickly and trust what the system is telling us.”
The Problem
Application exploits begin long before damage is visible
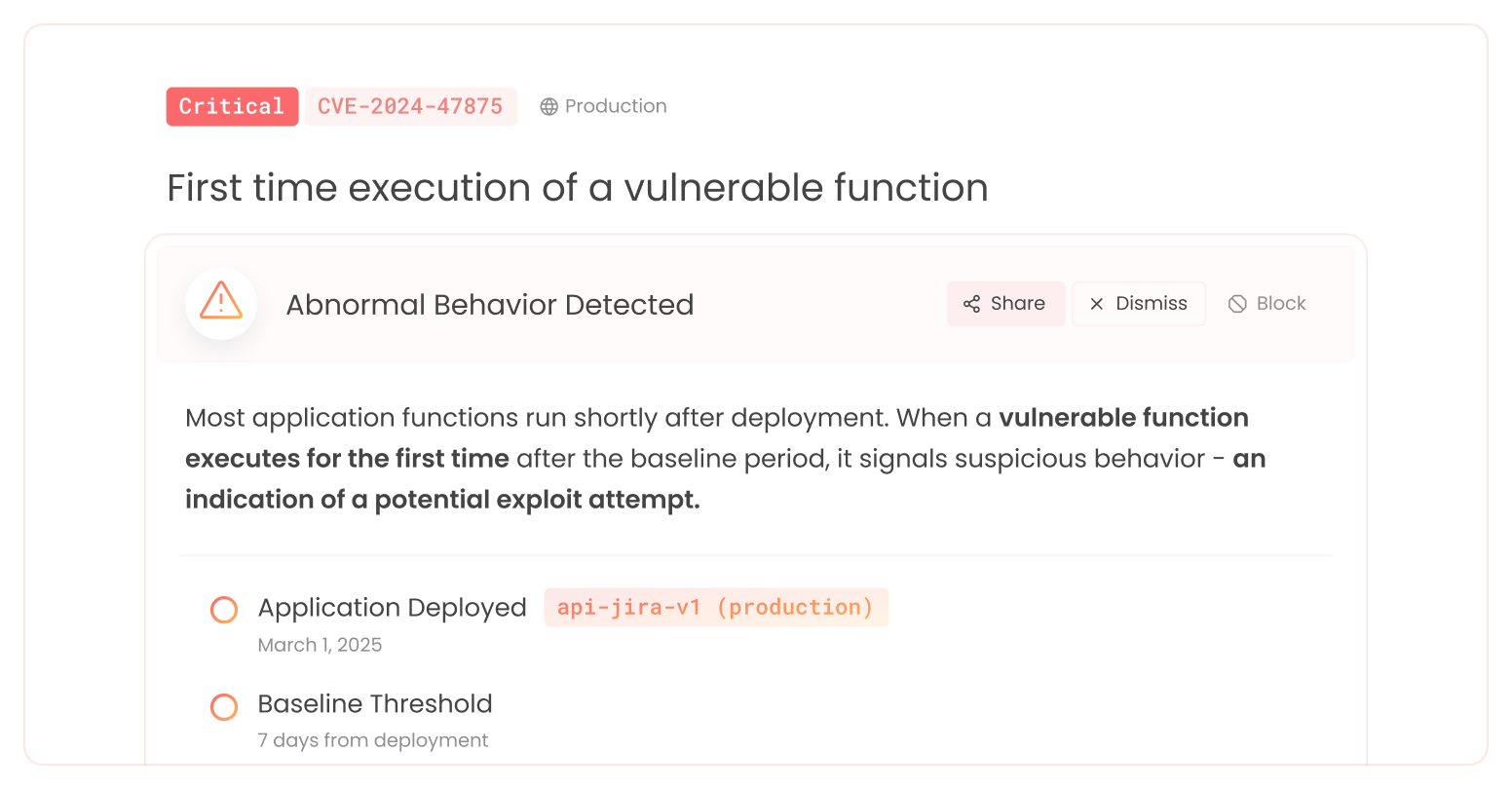
Traditional ADR tools monitor symptoms: outbound traffic, logs, crashes. But the exploit started earlier: when a vulnerable function was triggered, when logic was bypassed, or when user input reached a dangerous code path. Most tools miss this critical first step.
The Solution
Introducing Exploit Trigger Defense
Kodem ADR detects the initial trigger that launches the exploit path. This means no waiting for signatures or CVEs. No chasing logs after the fact. Just precise, real-time defense at the source.


First-Action Detection & Response
We capture the earliest sign of compromise by monitoring actual execution of vulnerable or sensitive functions.

CVE and Rule Agnostic
Kodem understands the normal behavior of every package and identifies when something deviates—even if it’s a zero-day or a logic flaw.

Built for Production
Lightweight, out-of-band, and deployable without application restarts or code changes.

Exploit-Aware Correlation
We combine runtime signals, code context, and execution flow to confirm exploitability with high precision and connect the point of exploit to the line of code causing it.
"Our solution redefines code security by merging SCA, SAST, and ADR into one accurate, high-performing platform."
"Kodem's platform offers one of the strongest solutions available, delivering real-world results with virtually no false positives."


Prevent exploitation, not just detect it

Zero performance impact on end users

No code instrumentation or restart required

Works across monoliths, microservices, and containers









