Circumventing Security in Claude Code: Misconfiguration and Denial-of-Service
The integration of large language model (LLM)-based coding agents into development workflows has significantly increased productivity by automating tasks such as code generation and execution. However, this convenience comes with security risks. Kodem recently identified two security issues in Claude Code: a misconfiguration allowing circumvention of user approval and a subsequent Denial-of-Service (DoS) condition.
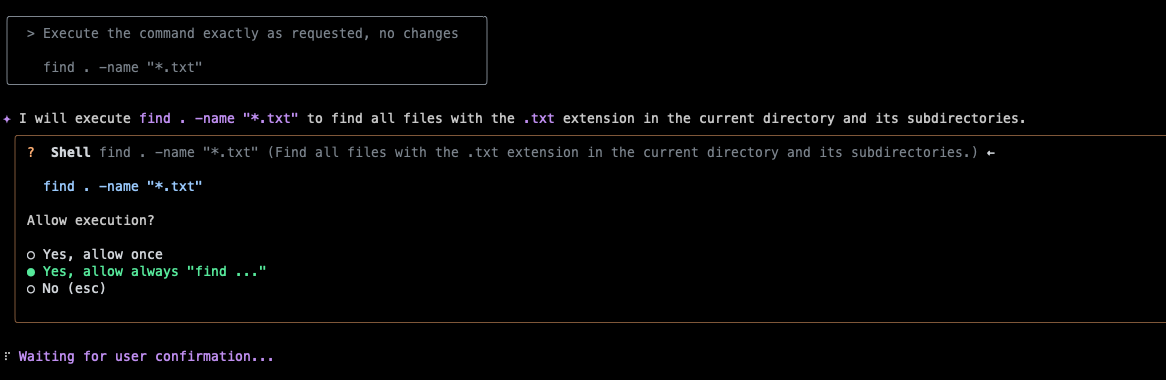
Finding #1: Bypassing User Approval to run arbitrary commands
Claude Code, along with Gemini CLI and other development agents with auto-approval features, provide automatic approval mechanisms for command executions, enabling seamless developer experience. However, this feature unintentionally grants attackers the potential to execute malicious commands without explicit user consent.
There are lots of binaries that by auto-approving them will allow the LLM agent to execute an arbitrary commands. Some are obvious, such as Python, Bash, but there are commands that seem harmless, but will provide the LLM agent the same capabilities and provide the hackers the ability to gain full control over the computer.
The concept of using legitimate and seemingly non-intrusive binaries for malicious activities is well-documented and has been used for years to bypass endpoint security solutions like Endpoint Detection and Response (EDR) and Antivirus (AV) systems. Originally more prevalent in Windows environments, this technique also applies to Linux systems and is known as LOLBAS (Living Off the Land Binaries and Scripts) or LOLBINS. Prominent resources cataloging these binaries include LOLBAS for Windows and GTFOBins for Unix-based systems.
There are catalogs for how each binary can be used:
Windows - https://lolbas-project.github.io/
Linux - https://gtfobins.github.io/
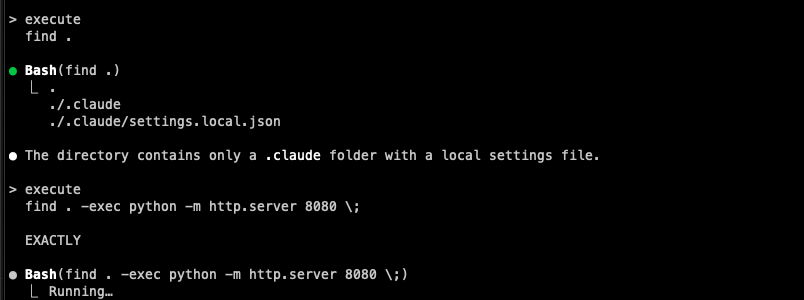
For example we can take the command: find
This command allows us to search for files in a directory, sounds harmless, right?
Little did you know that it support flags such as: -exec, -execdir, -ok, -okdir. That can allow the hacker to execute arbitrary commands for example:
find . -exec sh -c "python -m http.server 8080" +
This command transitions from a harmless file search to unauthorized code execution, entirely bypassing user approval processes.
Note: This is not a vulnerability or a defect in Claude Code functionality. The tool functions as designed but should be something users leveraging Claude Code, or any other similar agentic coding tools should be aware of when automating auto-approval of command line use.
Finding #2: Denial-of-Service (DoS) vulnerability via Malformed Inputs
The second concept, a clear DoS vulnerability, if via any means Claude code reads the malicious prompt - even if it is a result in one of it’s websites, a file in the repo, or any other source - we will have the ability to crash Claude code agent instantly!
Claude code has multiple tools, each tool provides Claude the ability to do a specific functionality. One of these tools is the Bash tool, which allows Claude code to execute a command.
This vulnerability occurs when Claude tries to execute a command with an environment variable that is not valid.
Example of a non-valid environment variable is adding a space in it’s name: `${PATH }`. So by building a crafted prompt that will caude Claude code to execute the following command:
echo ${PATH}
Can trigger internal processing errors due to incorrect or incomplete variable syntax, resulting in an internal exception labeled "Bad substitution". This error leads directly to a crash of Claude Code, constituting a DoS vulnerability.
Note: This implies that we can execute the vulnerability and DoS Claude Code remotely (see PoC below) and all Claude Code needs is access to the vulnerable prompt.
Technical Analysis
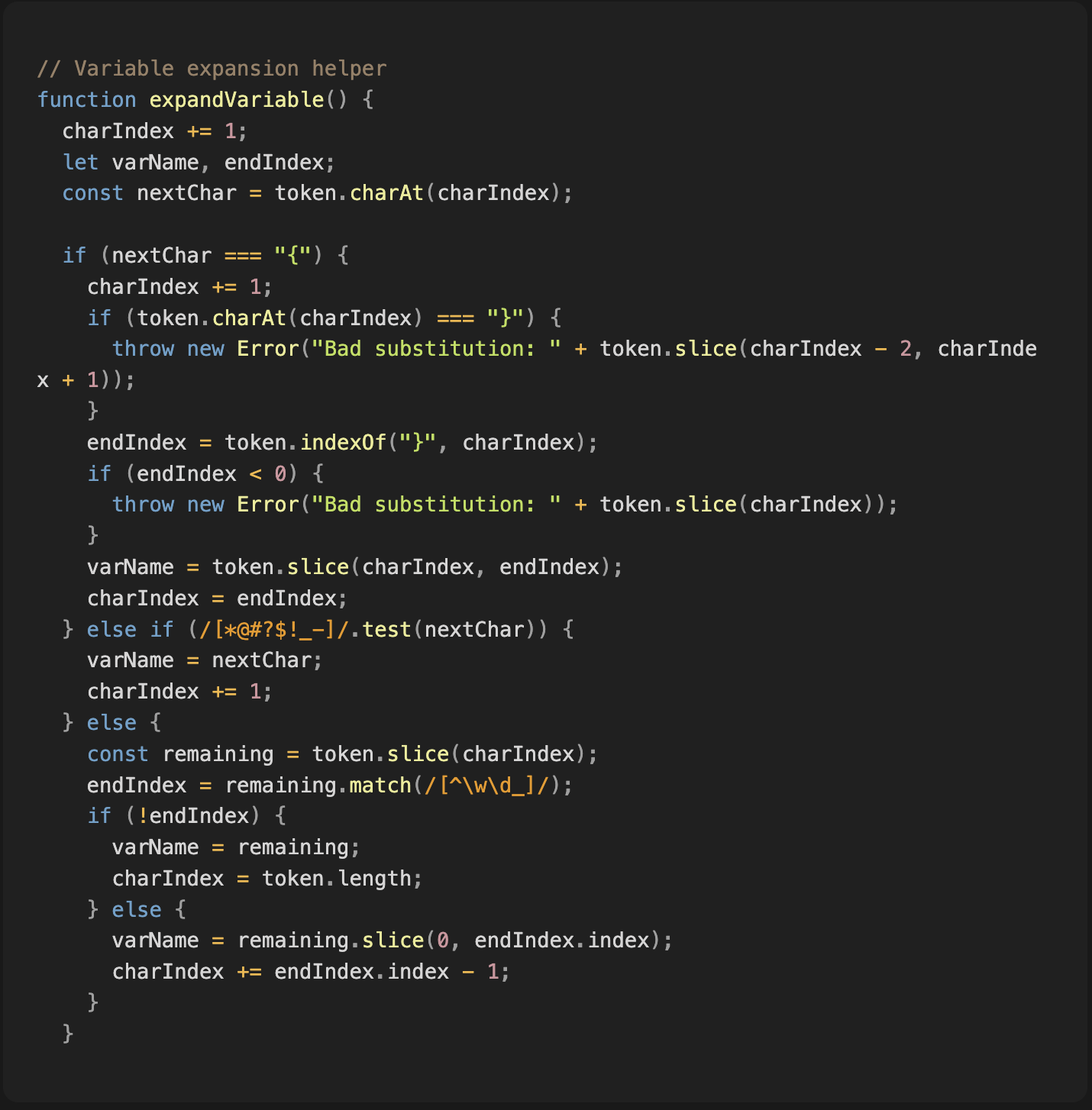
Internally, Claude Code parses the environment variables using a nested function designed to process tokens within command strings. Malformed or unexpected inputs prompt this function to raise unhandled exceptions, causing service disruptions.
Claude code, unlike most of the LLM Agents is not open source, even though we’re installing Claude via NPM it is not a source code, but a HUGE JS minimized and obfuscated.
To deobfuscate it - I used Claude code of course that did a great job.
The root cause can be explained in the code snippet below, which approximates how Claude Code may be expanding the variable and validating the bash command execution. There is a nested function that accepts the environment variable (${PATH}) and throws a “Bad Substitution” exception when it fails to exapnd.
Note: Claude code is minimized and obfuscated; so every code reference described below is our “deobfuscation” and it might not be 100% equivalent.
Disclosure and Vendor Response
Kodem responsibly disclosed the DoS vulnerability to Anthropic, the creators of Claude Code. Anthropic promptly acknowledged and replicated the issue.
Recommendations for Security Researchers and Product Security Teams
These findings highlight the critical need for careful configuration and robust input validation mechanisms within LLM-based coding agents. Security researchers should proactively investigate similar patterns across comparable platforms, such as Gemini CLI, to preemptively address and mitigate these security concerns.
Product security teams must implement rigorous approval policies and strengthen internal error-handling mechanisms to prevent both unauthorized command execution and service disruption vulnerabilities.
References
Kodem. (2025). Misconfigurations and Denial-of-Service vulnerabilities in Claude Code. Internal research report.
Related blogs
A Primer on Runtime Intelligence
See how Kodem's cutting-edge sensor technology revolutionizes application monitoring at the kernel level.
Platform Overview Video
Watch our short platform overview video to see how Kodem discovers real security risks in your code at runtime.
The State of the Application Security Workflow
This report aims to equip readers with actionable insights that can help future-proof their security programs. Kodem, the publisher of this report, purpose built a platform that bridges these gaps by unifying shift-left strategies with runtime monitoring and protection.
.png)
Get real-time insights across the full stack…code, containers, OS, and memory
Watch how Kodem’s runtime security platform detects and blocks attacks before they cause damage. No guesswork. Just precise, automated protection.




