Keep Risk Out of Main: When Security Policies Actually Help Development
Platforms can block merges when automated security checks fail, but they don't show whether your SCM policies are changing behavior over time. Kodem runs runtime-enriched PR/MR checks for code weaknesses, exposed secrets and open-source vulnerabilities, then turns policy outcomes into visible progress while work happens. Scan History reveals security trends across initiators and provides direct PR/MR links, so developers can see their own progress while AppSec blocks risky merges and investigates outcomes through detailed Kodem scan reports.
What Developers See From Check to Trend
When you push code, Kodem runs policy checks and blocks risky merges with detailed scan reports showing exactly what's wrong, how to fix it, and which issues matter most in production. After merging, Scan History shows your personal security improvement over time with links to track your historical scans.
What AppSec See From Policy to Trend
Scan History turns every check into security trends you can filter and analyze. See which initiators consistently pass, fail or need multiple attempts. Filter by policy result, scan type or resources aligned with your SCM structure, GitHub orgs and topics, Azure Repos projects and orgs, private or public repos and so on. Watch how teams handle runtime-critical issues versus indirect dependencies. Track which policies create lasting behavior change versus just blocking code. Move from one-off enforcement to understanding whether your security investment is actually working.
Policies that Change Behavior
The goal isn't just blocking bad code, it’s creating lasting security behavior change. Configure Source Control Management (SCM) policies in Kodem that matter in development, not just security enforcement.
- Require a fix version to exist before flagging vulnerabilities.
- Raise the bar by severity and factor in exploitation maturity and EPSS scores.
- Give extra weight when packages are direct dependencies.
- Key off OWASP categories and CWE IDs for code weaknesses.
- Enforce license terms or block known malicious packages.
The result is guidance developers can act on and enforcement that only blocks merges that should be blocked.
Positive behavior change looks like:
- Developers passing checks on the first attempt more often.
- Time-to-green decreases as teams learn faster fixes.
- Repeat failures for the same issue types are reduced.
- Proactive security practices are increasing.
What platforms can't answer:
- Are developers getting better at security over time?
- Is this policy teaching teams, or just blocking them?
- Which teams are improving vs. struggling with the same issues?
Patterns that Prove Improvement
Since policy scans of PRs/MRs occur before merge, the scoreboard reflects your organization's security posture at the gate:
- Pass rates trending up across recent days.
- Warn-and-pass reducing as teams fix earlier.
- Time to green falling from first failed check to passing commit.
- Recurring failures spotted by repository or org, with PR links to see what fixed them.
- Which initiators improve week after week and where second attempts were needed.
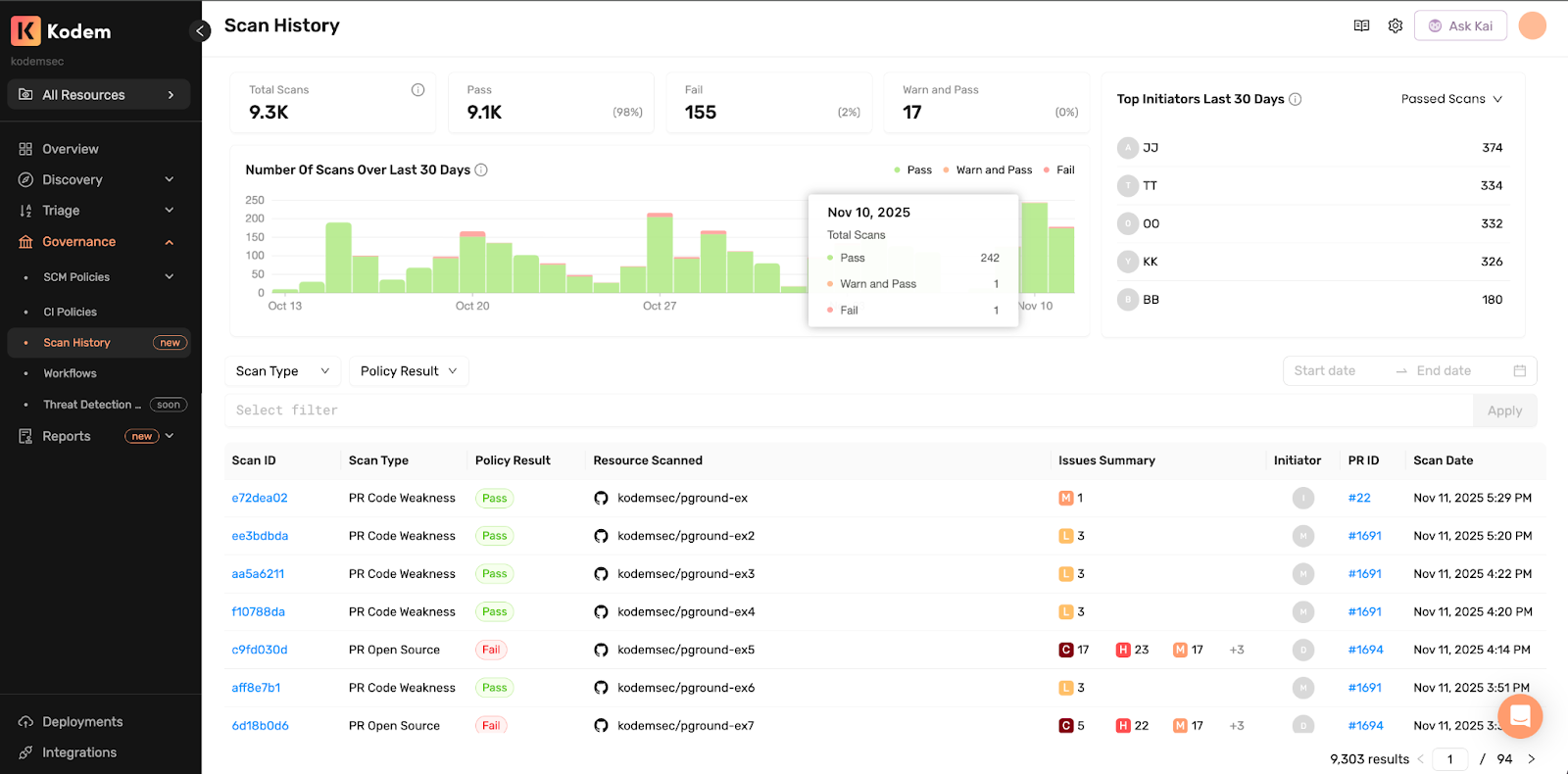
What AppSec Can Answer in Seconds
- Which resources are passing on the first attempt.
- Which initiators regularly produce failing checks and how quickly they recover.
- Which policies catch the most issues, such as malicious packages, exposed secrets and license violations.
- Where runtime-used packages are driving the most remediation action.
All of it traceable to a PR/MR with the issue summary and the time it ended.
Outcomes in Practice
Developers see their progress in passing and warn-and-pass scans and can investigate past successful remediation through PR/MR links. AppSec gets visibility into organizational security trends and guardrails that stop risky merges. Leaders get clear progress on security behavior change while work happens.
Related blogs
When AppSec Implementation is Lightweight
Despite promising fast value, modern AppSec platforms often demand lengthy, high-friction onboarding. Teams are left managing alert noise, continuous configuration debt and fractured integrations. This friction stems from flawed implementation models, whether layered on top of the technology or baked into it, shaping how these platforms are adopted and operated.
4
.png)
From SBOM Inventory to Package Intelligence
How Kodem turns SBOM packages into the control plane for investigation, governance and remediation

Kai at Work: A Day in the Life of an AI AppSec Engineer
Kai, Kodem’s secure-by-design AI AppSec Engineer, is integrated directly into the platform to deliver contextualized and actionable answers precisely when AppSec teams need them. By converting your existing security data into conversational intelligence, Kai eliminates the need for hours of manual investigation and context-switching. You can now ask questions as you would to a senior, humble, and tireless engineer.
A Primer on Runtime Intelligence
See how Kodem's cutting-edge sensor technology revolutionizes application monitoring at the kernel level.
Platform Overview Video
Watch our short platform overview video to see how Kodem discovers real security risks in your code at runtime.
The State of the Application Security Workflow
This report aims to equip readers with actionable insights that can help future-proof their security programs. Kodem, the publisher of this report, purpose built a platform that bridges these gaps by unifying shift-left strategies with runtime monitoring and protection.
.png)
Get real-time insights across the full stack…code, containers, OS, and memory
Watch how Kodem’s runtime security platform detects and blocks attacks before they cause damage. No guesswork. Just precise, automated protection.




