Remediation That Meets Developers in Context
Identifying issues isn’t the challenge. The challenge is effective remediation that fits your codebase, your environment and your team’s development velocity. Developers need to understand where issues originated, which packages to upgrade, what code to change and how disruptive fixes will be. Meanwhile, AppSec needs visibility into what's immediately actionable and which issues require cross-team coordination.

Beyond Fix Versions
Most tools surface fix versions and leave the rest to the development team. Kodem goes further by combining publicly available fixes with source tracing, environment-specific context and verified upgrade paths that reflect your actual repositories and images. This gives developers the smallest safe change to apply, while AppSec gains clear visibility into how remediation is progressing.
- For code issues (SAST), Kodem provides exact fix locations, line-level guidance and specific code changes.
- For open-source issues (SCA): you get verified upgrade paths, recommended package versions and direct or transitive dependency updates and visibility into which base image the component depends on.
How Kodem Builds Contextual Remediation
Kodem analyzes your software bill of materials across repositories and images, detecting package vulnerabilities, malicious packages, code weaknesses, and exposed secrets. When issues are found, the platform traces them back to their entry point.
For packages, Kodem determines whether dependencies are direct or transitive, identifies secure base images and verifies exact versions that resolve vulnerabilities. For custom-built images, remediation paths account for transitive dependencies and base image lineage. Every issue is aggregated with its origin, its verified fix version and the cleanest update path, creating a remediation plan that reflects reality, not assumptions. By aggregating every issue with its origin and verified fix version, we establish the cleanest update path. This creates a remediation plan based on reality, not assumptions.
Package (SCA) Remediation Without Trial and Error
You see:
- Vulnerability source: Direct or transitive dependency origin.
- Upgrade target: Safest version that resolves the issue.
- Remediation path: Whether base image updates or targeted package upgrades eliminate the risk entirely.
Developers can update files like requirements.txt, package.json, go.mod or container definitions with confidence without experimenting across services.

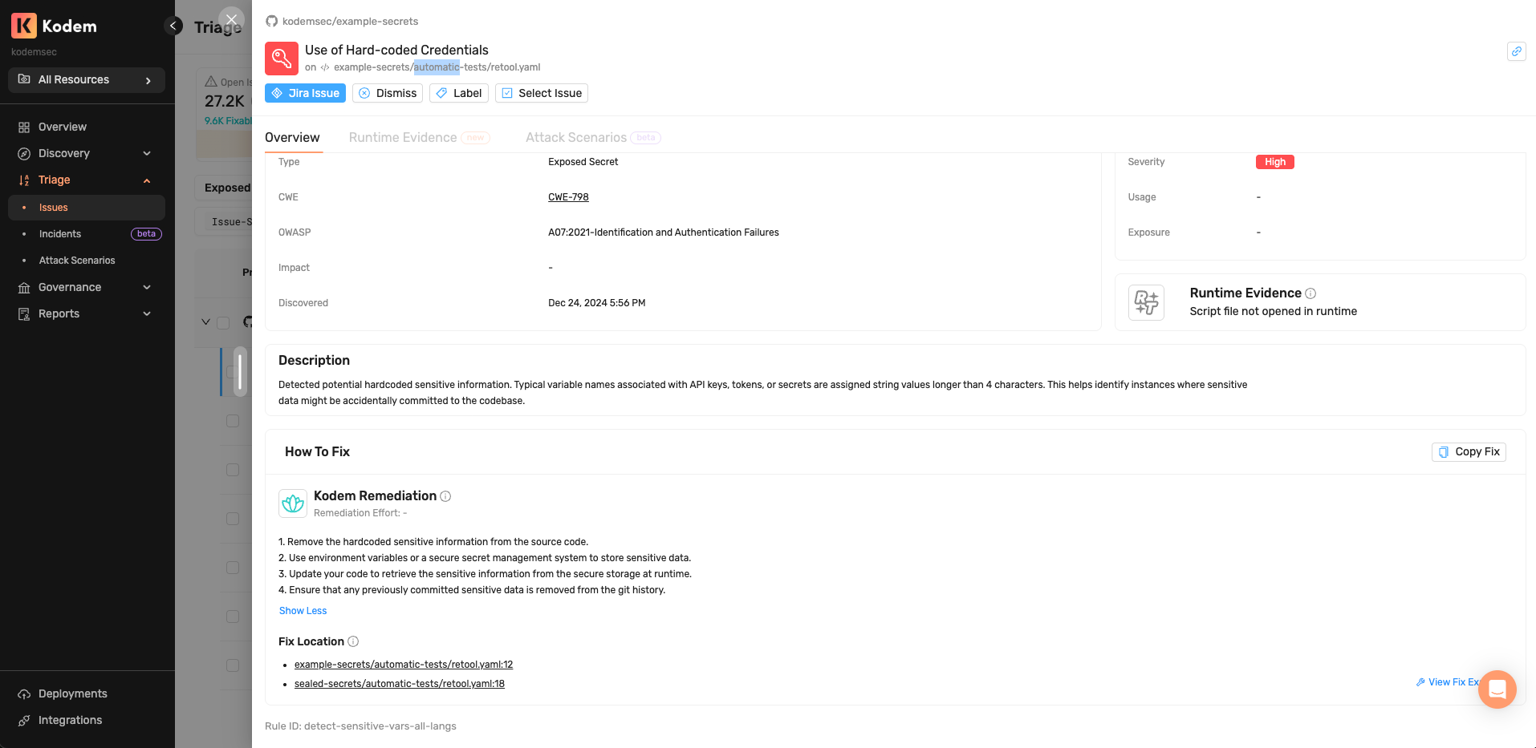
Code (SAST) Fixes That Go Straight to the Source
When the issue is in your own code, the guidance points directly to the source. You see the file and line references, an explanation of the weakness and actual code samples showing exactly how to fix the issue in your specific language and framework. Developers open the file, apply the fix and keep moving.
What you get:
- Precise file and line locations.
- Generated code samples with before/after examples specific to your source code.
- Copyable fix instructions you can apply directly.
Review and implementation:
- Copy code samples and implement them directly in your IDE.
- Create Jira issues that include the complete remediation instructions.
- With Source Control integration and SCM policies configured, view fixes in Kodem Scan Reports during PR/MR scanning.
Effort You Can Plan Around
Every remediation is tagged as Patch (minimal risk), Minor (light testing recommended) or Major (breaking changes need coordination). Teams can filter for immediate wins or plan larger updates accordingly.
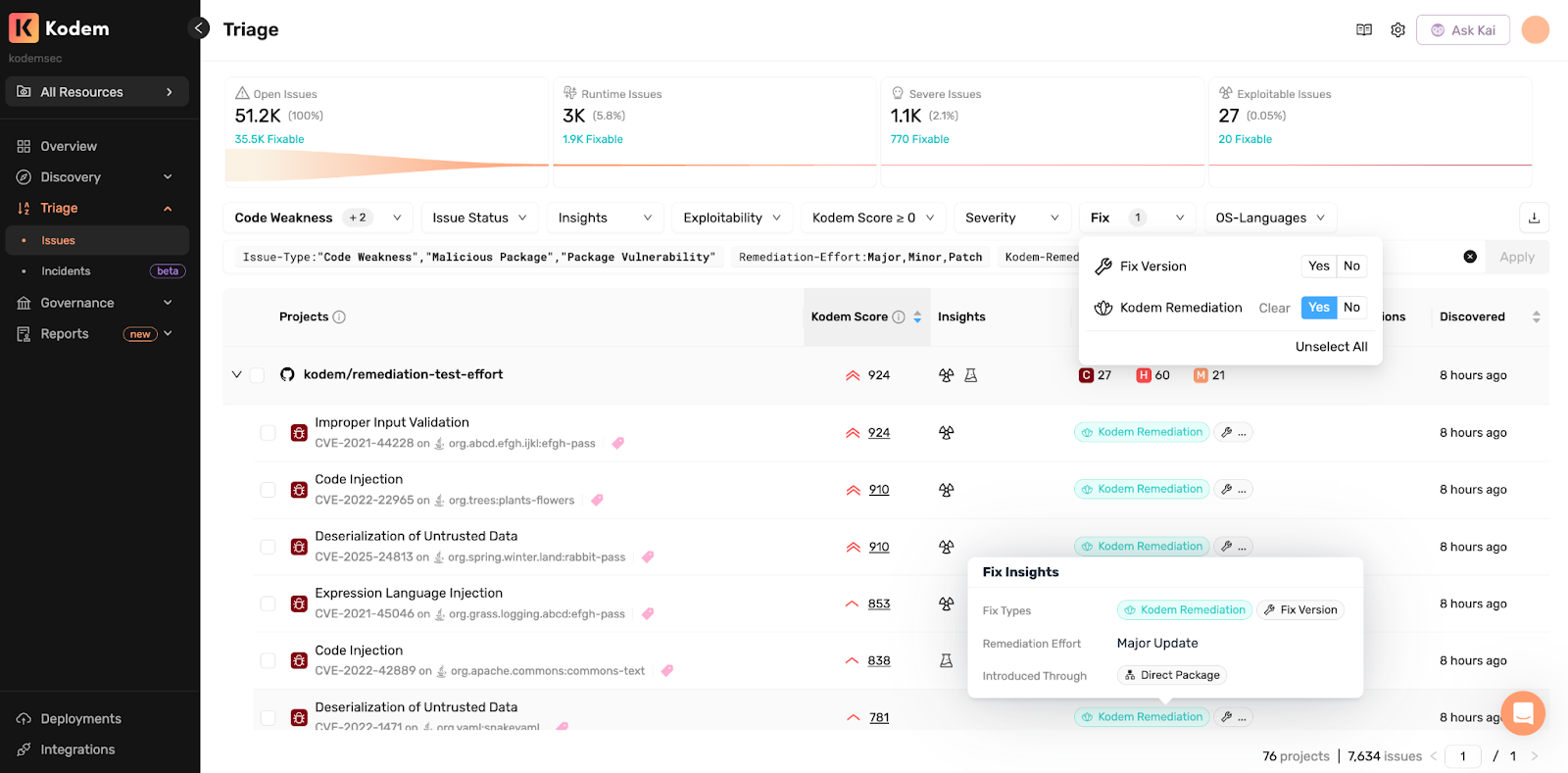
Find What’s Fixable Right Now
Triage becomes faster when guidance is actionable:
- Filter for Fix Version and Kodem Remediation to help teams surface issues with verified upgrade paths.
- If the goal is clearing quick wins for a sprint, filtering by Patch effort gives developers a clean list of changes that can ship immediately.
- When planning for larger updates, Minor and Major fixes are already sorted and ready for triaging.
Why This Transforms Workflows
For Developers: Clear answers replace guesswork. Which file needs updating? What version resolves the issue? How much effort will this require? Remediation becomes a scoped development task instead of a research project.
For AppSec: Predictable progress tracking with verified paths. Point developers to the fastest safe changes, route complex fixes to appropriate owners and measure real progress through features like Scan History.
Remediation Without Friction
Kodem transforms vulnerability management from a guessing game into trial-and-error into informed workflow. Developers spend less time hunting for context and more time resolving issues. AppSec gets measurable ways to ensure vulnerabilities are systematically resolved across environments.
Related blogs
When AppSec Implementation is Lightweight
Despite promising fast value, modern AppSec platforms often demand lengthy, high-friction onboarding. Teams are left managing alert noise, continuous configuration debt and fractured integrations. This friction stems from flawed implementation models, whether layered on top of the technology or baked into it, shaping how these platforms are adopted and operated.
4
.png)
From SBOM Inventory to Package Intelligence
How Kodem turns SBOM packages into the control plane for investigation, governance and remediation

Kai at Work: A Day in the Life of an AI AppSec Engineer
Kai, Kodem’s secure-by-design AI AppSec Engineer, is integrated directly into the platform to deliver contextualized and actionable answers precisely when AppSec teams need them. By converting your existing security data into conversational intelligence, Kai eliminates the need for hours of manual investigation and context-switching. You can now ask questions as you would to a senior, humble, and tireless engineer.
A Primer on Runtime Intelligence
See how Kodem's cutting-edge sensor technology revolutionizes application monitoring at the kernel level.
Platform Overview Video
Watch our short platform overview video to see how Kodem discovers real security risks in your code at runtime.
The State of the Application Security Workflow
This report aims to equip readers with actionable insights that can help future-proof their security programs. Kodem, the publisher of this report, purpose built a platform that bridges these gaps by unifying shift-left strategies with runtime monitoring and protection.
.png)
Get real-time insights across the full stack…code, containers, OS, and memory
Watch how Kodem’s runtime security platform detects and blocks attacks before they cause damage. No guesswork. Just precise, automated protection.




