Detect Exposed Secrets
Secret safety on auto-pilot
Prevent, detect, and revoke exposed credentials across code, configs, CI, and runtime.

The problem legacy tools create
Secrets leak in commits, logs, and images.
Tokens remain valid long after they’re removed from repos.
Our approach solves the problems
1
Full SDLC Detection
Detect secrets and hard coded credentials in Dev, Test and Prod
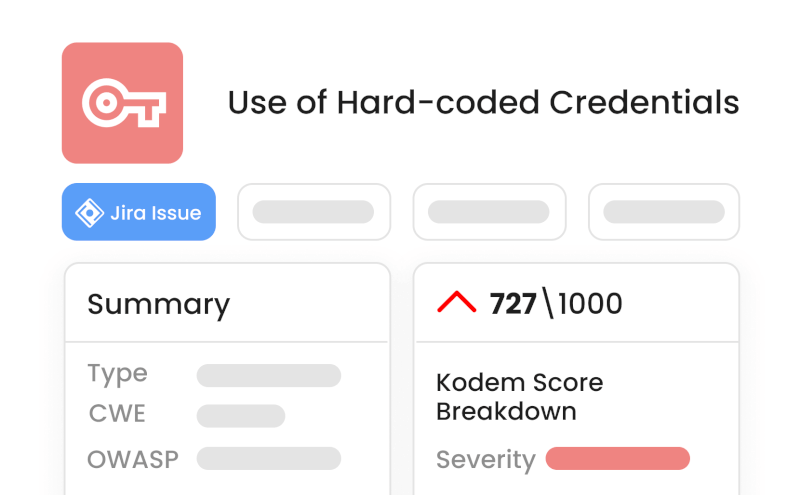
2
Stop builds with exposed secrets
Pre-commit and PR scanning to block merges.
3
Robust audit trails
Historical scanning of Git repos and container images.
4
Auto-generated fix
Choose AI generated code fixes. Never modifies your repo or uses code for training.

Trusted by
















































How Kodem helped
An AWS key was committed in a PR.
Kodem blocked the merge and automatically revoked and rotated the credential across the environment.
Reduce mean time to revoke from days to minutes
Close the loop from detection → revocation → verified remediation
Prevent credential leaks from becoming breaches
"No other tool showed us how low-severity issues could escalate into real production impact. Kodem caught it in time."


