Automate Vulnerability Management
Neutralize attack chains, not vulnerabilities
Discover and auto-fix critical attack chain scenarios across your entire environment with Kodem’s unified posture management


The problem legacy tools create
Findings remain siloed across code, containers, and cloud.
Patches aren’t always available, leaving open exposures.
Our approach solves the problems
1
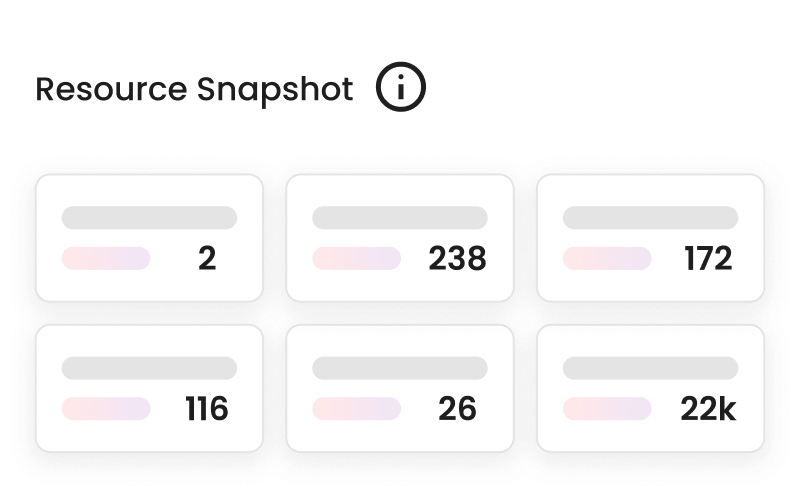
Full-stack inventory
Unified inventory across environments.
2
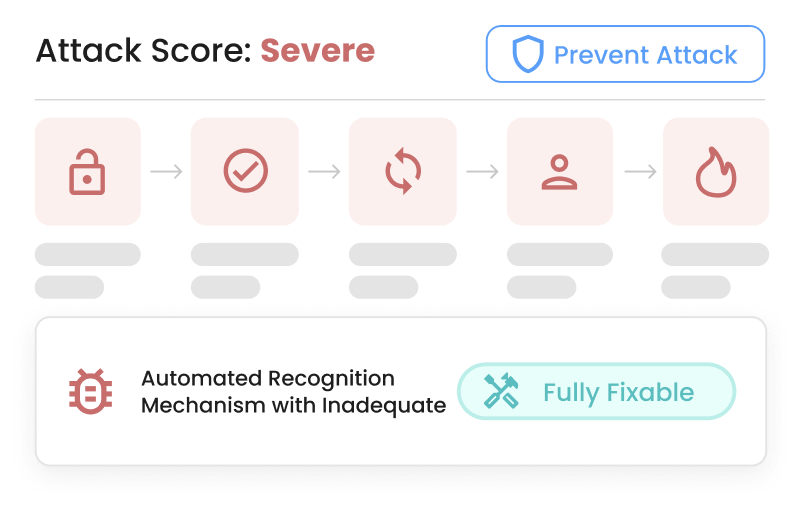
Attack chain modeling
Simulate attack chains to surface real exploit paths.
3
Virtual patching
Auto-fix mitigations when patches lag.

4
Full-SDLC Governance
Enforce consistent policy from dev to prod.
Trusted by
















































How Kodem helped
An Alpine image with a privilege escalation bug had no patch available.
Kodem generated a fix by removing setuid and adjusting capabilities until the vendor released a patch.
Detect 100% of attack chains missed by SAST/SCA
Avoid $1M+ breach scenarios missed by legacy tools
Auto-fix reduces exposure windows
"No other tool showed us how low-severity vulns could be chained into a breach. Kodem did."


