Kai at Work: A Day in the Life of an AI AppSec Engineer
Kai, Kodem’s secure-by-design AI AppSec Engineer, is integrated directly into the platform to deliver contextualized and actionable answers precisely when AppSec teams need them. By converting your existing security data into conversational intelligence, Kai eliminates the need for hours of manual investigation and context-switching. You can now ask questions as you would to a senior, humble, and tireless engineer:
- What should I work on first?
- Does React2Shell / Shai Hulud 2.0 npm supply chain attack affect our environment?
- How do I fix this issue?
- What’s our risk exposure?
This article walks through how teams use Kai in a typical day: triage and prioritization, responding to headline CVEs, moving from insight to remediation, setting guardrails that developers can live with and sharing clear status updates.
Problem: AppSec Work Breaks Down at the “So What?”
Most security tools can tell you what exists. Fewer can tell you what matters in your environment, right now. AppSec teams are under pressure as volume rises, headcount stays flat and teams need more than CVSS, rather towards contextual exploitability. That gap shows up the same way every day:
- Triage starts with noise.
- Prioritization defaults to severity labels.
- Headline CVEs trigger research marathons and fire-drills.
- Translating findings into developer-ready work becomes growing tech. debt.
Kai’s job is to close that gap operationally: turn findings into decisions and decisions into actionable work, without turning AppSec into a constant context-switching exercise.
Where Kai Fits In
Kai enhances the usability of Kodem CORE, Kodem's contextual observability and remediation engine. By sitting on top of the engine, Kai enables teams to ask plain-language questions and receive answers based on the real-world context of their environment, correlating signals across code, packages, containers and runtime.
Kai incorporates enterprise-level security. Your data remains exclusively yours - never shared, never exposed, never used for training AI models.
You interact with Kai in two ways:
- Ask Kai: A chat pane inside Kodem for natural-language questions scoped to what you’re viewing, whether that’s an issue, an application, or overall posture.
- Kai in-context: Actionable intelligence as you work - flagging which findings are Confirmed or Likely False-Positive during triage, helping you prioritize during investigation and guiding remediation. Whether you're unsure where to start, need answers fast or are new to the platform, any task becomes accessible.
A Day with Kai: Five Real Scenarios
Use Case 1: A New CVE Lands “Are We Actually Affected?”
This is the moment every AppSec team recognizes. A high-profile vulnerability hits your feed. Leadership asks for an answer. Customers ask for reassurance. Engineers ask for confirmation.
Ask Kai:
- Do we currently have any instances of CVE-2025-55182 (React2Shell) in our environment? If so, what is impacted?
- Do we have any exposure related to the Shai Hulud 2.0 npm supply chain attack? If so, which repositories / images include the affected packages?
Kai correlates the response with your environment's context, including runtime evidence. Optionally, enable Web Search to enrich answers with trusted public sources such as NVD, CISA, KEV and more.
Kai responds with what teams actually need:
- Whether the vulnerability exists in your environment.
- Where it exists.
- What to do next.
Asking Kai if React2Shell is present in the environment
Use Case 2: Triage Without The Noise
The initial chaos has subsided. You are faced with over 200 new findings from the past week and a familiar level of uncertainty. Rather than manually clicking through every issue, Kai delivers a preliminary analysis directly in the Triage Issues page.
Ask Kai:
- What should I prioritize from last week's findings?
Kai flags individual occurrences as Confirmed or Likely False-Positive, with reasoning so triage starts from signal instead of noise. With no need to rebuild context in another tool, teams can immediately label, dismiss, create tickets and automations. For example, you can create a workflow to automatically dismiss new or modified code issues that Kai flags as Likely False-Positive.
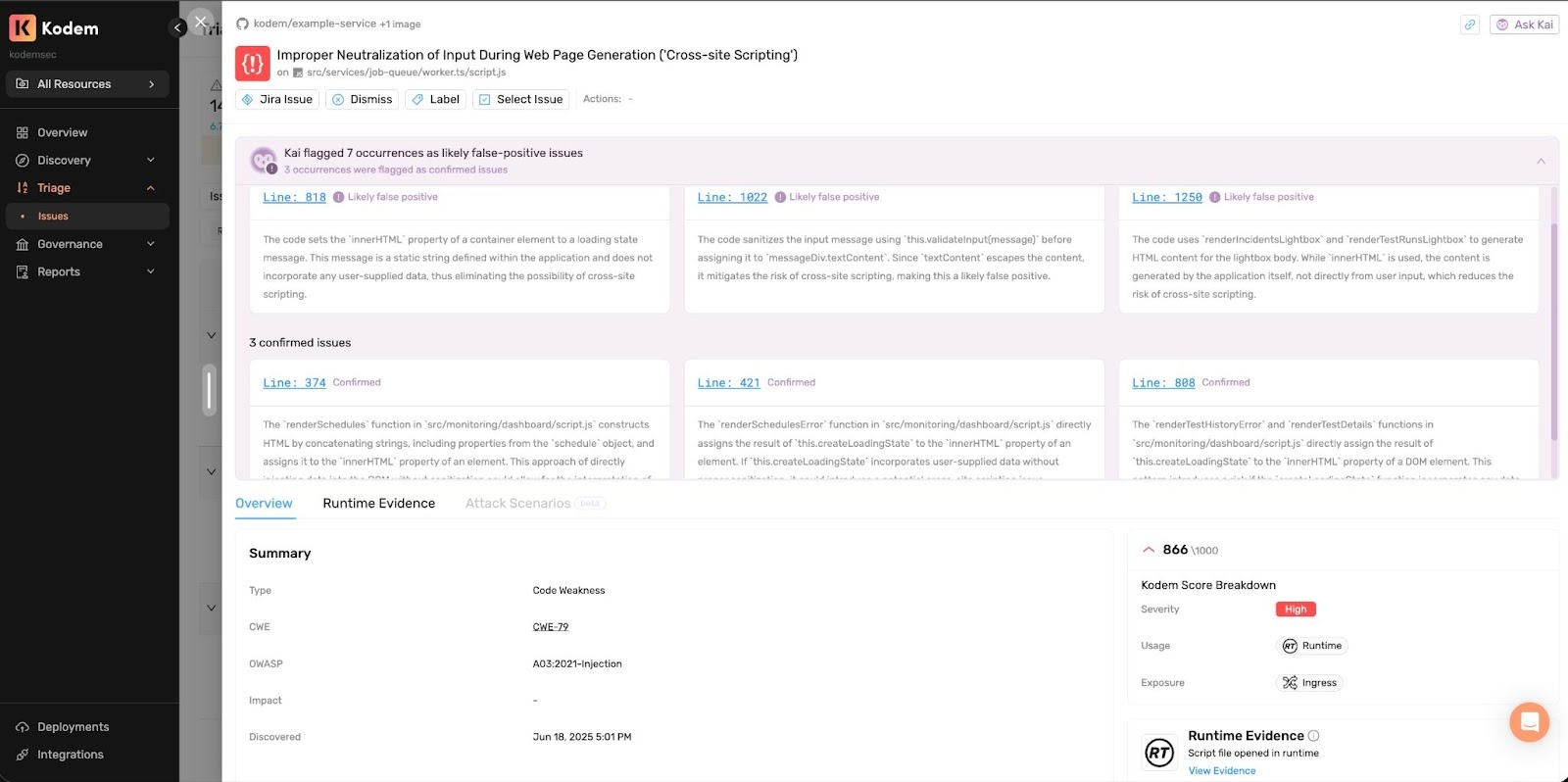
Use Case 3: From Insight to a Concrete Fix
Knowing you’re exposed is not the same as knowing what to do next. This is where teams usually burn time:
- Finding the safest upgrade path.
- Understanding blast radius.
- Deciding what’s “smallest safe change” versus a risky refactor.
- Translating the plan into developer-ready work.
Kai is strongest when it turns investigation into a concrete next step:
- What to change.
- Where to change it.
- Whether the fix resolves the issue entirely.
- What to verify after shipping.
How can I fix code issues with Kai?
Kai can draft a ticket from any context in the platform and suggest an assignee based on repository contribution. The ticket includes a developer-ready summary, security impact such as affected packages and runtime usage, remediation guidance with base image updates and package versions, and a link to the corresponding Kodem issue.
Use Case 4: Guardrails Developers Can Live With
AppSec often shifts from response to prevention: tuning repository guardrails that reduce risk without blocking delivery. With Kai reviewing each finding to assess relevancy, SCM policies can be more precise without being noisy, enforcing scans while applying protection and suppression conditions that reflect intent:
- Block merges when a new confirmed high-impact risk is introduced.
- Warn on recurring noise when contextual evidence supports a likely false-positive, so the same low-value alerts do not resurface every scan.
Use Case 5: Explaining Risk Without Starting From A Blank Page
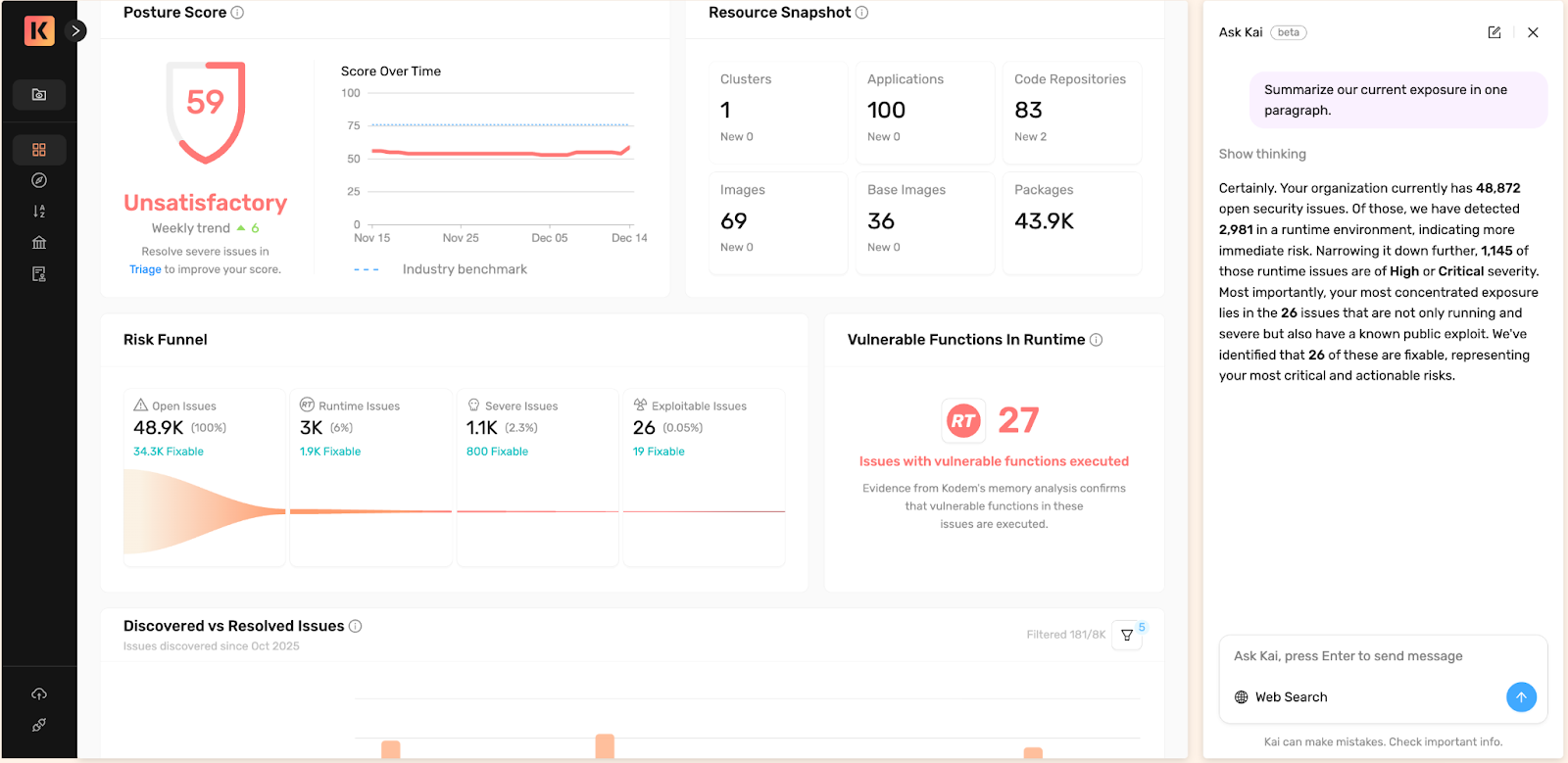
When it comes to status updates, Kai helps teams generate clear, grounded summaries, so updates reflect what is true in the environment rather than a stitched-together narrative from multiple dashboards:
- Can you explain my posture score?
- Summarize our current exposure in one paragraph.
- Can you summarize the state of my runtime risks?
What Changes When Kai Is in the Loop
By day’s end, the transformation is not “more AI,” it’s operational clarity:
- Less time sorting and more time acting.
- Faster answers to headline risk with proof you can share.
- Remediation that’s shippable, not theoretical (Verified by Kodem Research Team).
- Guardrails that scale across teams without constant escalation.
- Clearer communication, because you’re not rebuilding context from scratch
Kai’s role is simple: be the extra pair of hands AppSec teams need, always on, always in context and always ready for the question that matters most: “What do we do next?”
Related blogs
.png)
From SBOM Inventory to Package Intelligence
How Kodem turns SBOM packages into the control plane for investigation, governance and remediation
CVE-2026-21858: Ni8mare: Unauthenticated Remote Code Execution in n8n
An unauthenticated Remote Code Execution (RCE) flaw, tracked as CVE-2026-21858 (CVSS 10.0), has been discovered in n8n, the widely-adopted workflow automation platform. With over 100 million Docker pulls and an estimated 100,000 locally deployed instances, this vulnerability transforms n8n from a productivity tool into a severe single point of potential failure for organizations globally.

Guess Who's Back: Shai-Hulud 3.0 The Golden Path
Security analysts recently identified a new variant of the Shai-Hulud npm supply chain worm in the public registry, signaling continued evolution of this threat family. This variant, dubbed “The Golden Path” exhibits modifications from prior waves of the malware, suggesting ongoing evolution in the threat actor’s tradecraft.
A Primer on Runtime Intelligence
See how Kodem's cutting-edge sensor technology revolutionizes application monitoring at the kernel level.
Platform Overview Video
Watch our short platform overview video to see how Kodem discovers real security risks in your code at runtime.
The State of the Application Security Workflow
This report aims to equip readers with actionable insights that can help future-proof their security programs. Kodem, the publisher of this report, purpose built a platform that bridges these gaps by unifying shift-left strategies with runtime monitoring and protection.
.png)
Get real-time insights across the full stack…code, containers, OS, and memory
Watch how Kodem’s runtime security platform detects and blocks attacks before they cause damage. No guesswork. Just precise, automated protection.

Stay up-to-date on Audit Nexus
A curated resource for the many updates to cybersecurity and AI risk regulations, frameworks, and standards.


