When AppSec Implementation is Lightweight
Eliminating deployment and maintenance hurdles at scale
Despite promising fast value, modern AppSec platforms often demand lengthy, high-friction onboarding. Teams are left managing alert noise, continuous configuration debt and fractured integrations. This friction stems from flawed implementation models, whether layered on top of the technology or baked into it, shaping how these platforms are adopted and operated.
The uncomfortable Truth About AppSec Onboarding
Most modern AppSec platforms make it easy to connect systems. Source control, container registries, environments and users are quickly marked as “done.” But connection is not implementation.
In many organizations, meaningful visibility arrives only after teams are already overwhelmed. Hundreds of repositories, pipelines, containers, tickets and dashboards accumulate faster than teams can make sense of them. By the time security leaders step back to assess risk, much of that surface area is already noisy, unused or ignored.
We’ve spoken with security teams who realized months after rollout that most of the data they worked hard to integrate was never referenced in decisions, never acted on and never fully trusted. Workflows, policies and integrations are frequently established on mere assumptions, resulting in visibility that arrives too late, if at all. Consequently, what should have been a quiet implementation becomes a persistent operational burden.
In practice, many AppSec platforms require substantial post-connection work before visibility becomes usable at scale. Teams manually import repositories, configure projects and policies and tune noise just to reach a baseline they can trust. Connection alone doesn’t create clarity and without clarity, implementation stalls. That gap is what makes onboarding feel complex long after setup is technically complete.
Visibility First
Traditional AppSec onboarding expects teams to wire together repositories, policies, ticketing systems and CI gates to understand risk, while visibility emerges only after configuration, tuning and workflow alignment. Kodem takes the opposite approach.
Instead of forcing teams to pre-define their entire security process before learning anything about their environment, Kodem delivers runtime-enriched visibility early. This becomes the foundation for decision-making, allowing teams to operationalize security with intention, grounded in evidence rather than assumptions. In practice, this means remediation happens in context, guided by execution evidence and delivered where developers already work, rather than pushed through disconnected dashboards or premature workflows.
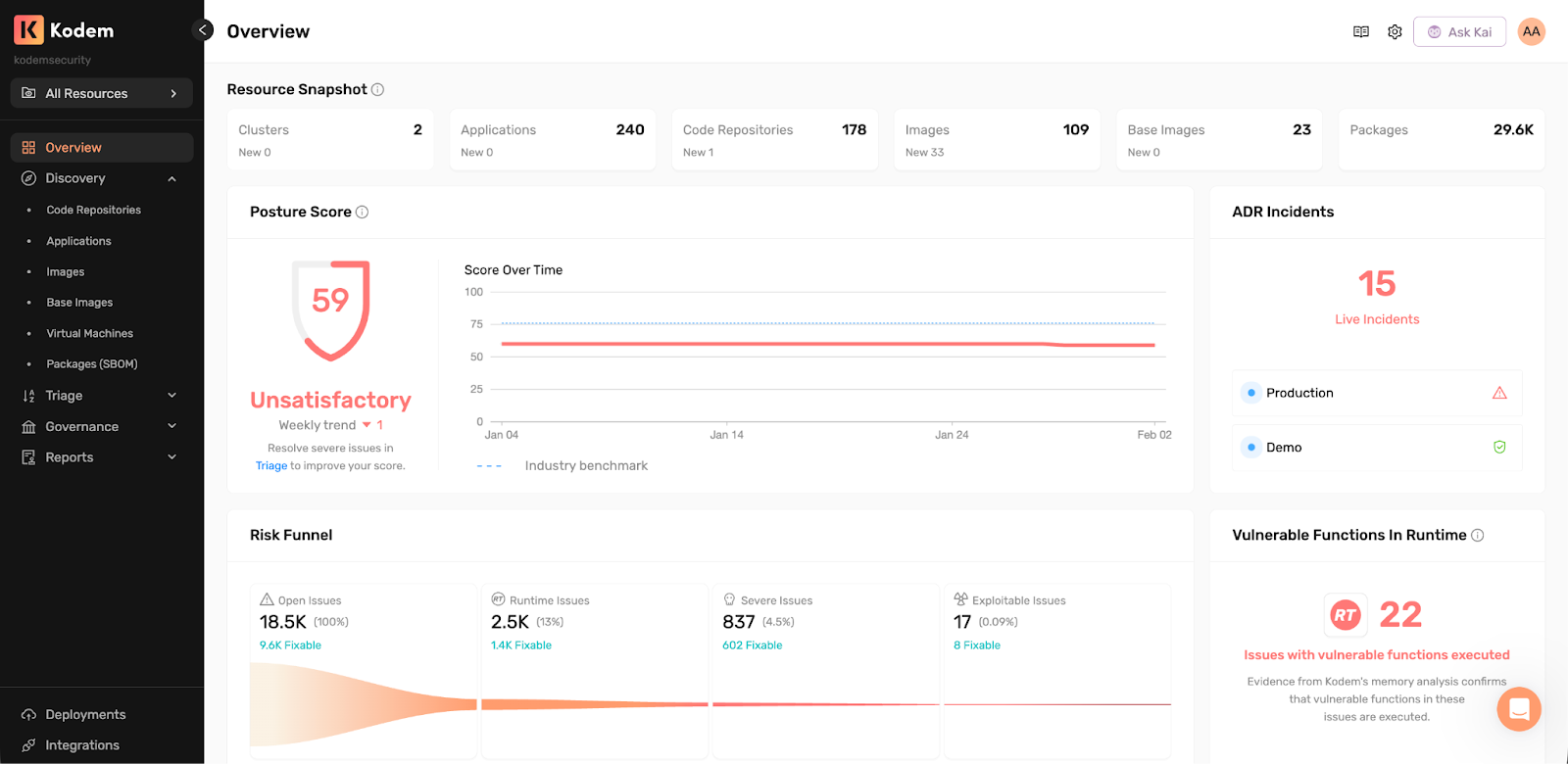
How Kodem Works, Without the Wait
Kodem is a unified application security platform that incorporates code analysis and runtime intelligence across the entire application stack.
Kodem combines:
- Static Application Security Testing (SAST) to identify weaknesses in proprietary and third-party code.
- Software Composition Analysis (SCA) to surface risk across direct and transitive open source dependencies.
- Container and image security to analyze build artifacts, base images and binaries.
- Runtime behavior and memory insights to understand real execution paths, exploitability and malicious activity.
By correlating code findings with real execution data, Kodem focuses security teams on what is actually exploitable in their environment. This reduces noise and false-positives, eliminating the need for extensive post-deployment tuning just to make findings actionable. The result is clarity early in the process, when it matters most.
What teams get early:
- Function-level runtime evidence that shows whether vulnerable code paths are reachable.
- Clear exposure context tied to real services, containers and workloads.
- Coverage across open-source dependencies, proprietary and third-party code, including AI-generated code and containers.
- End-to-end SDLC visibility, spanning development through production.
Implementation at a Glance
Kodem adapts to your stack and team structure, delivering value with minimal upfront effort.
1. Connect your source code
Install the Kodem Security app from your source control marketplace to connect source code and surface application context across platforms such as GitHub, GitLab, Azure DevOps and Bitbucket Cloud.
Once connected, Kodem shows and enables:
- Asset discovery.
- Dependency hierarchy mapping and SBOM generation.
- PR/MR security checks.
- Continuous code scanning.
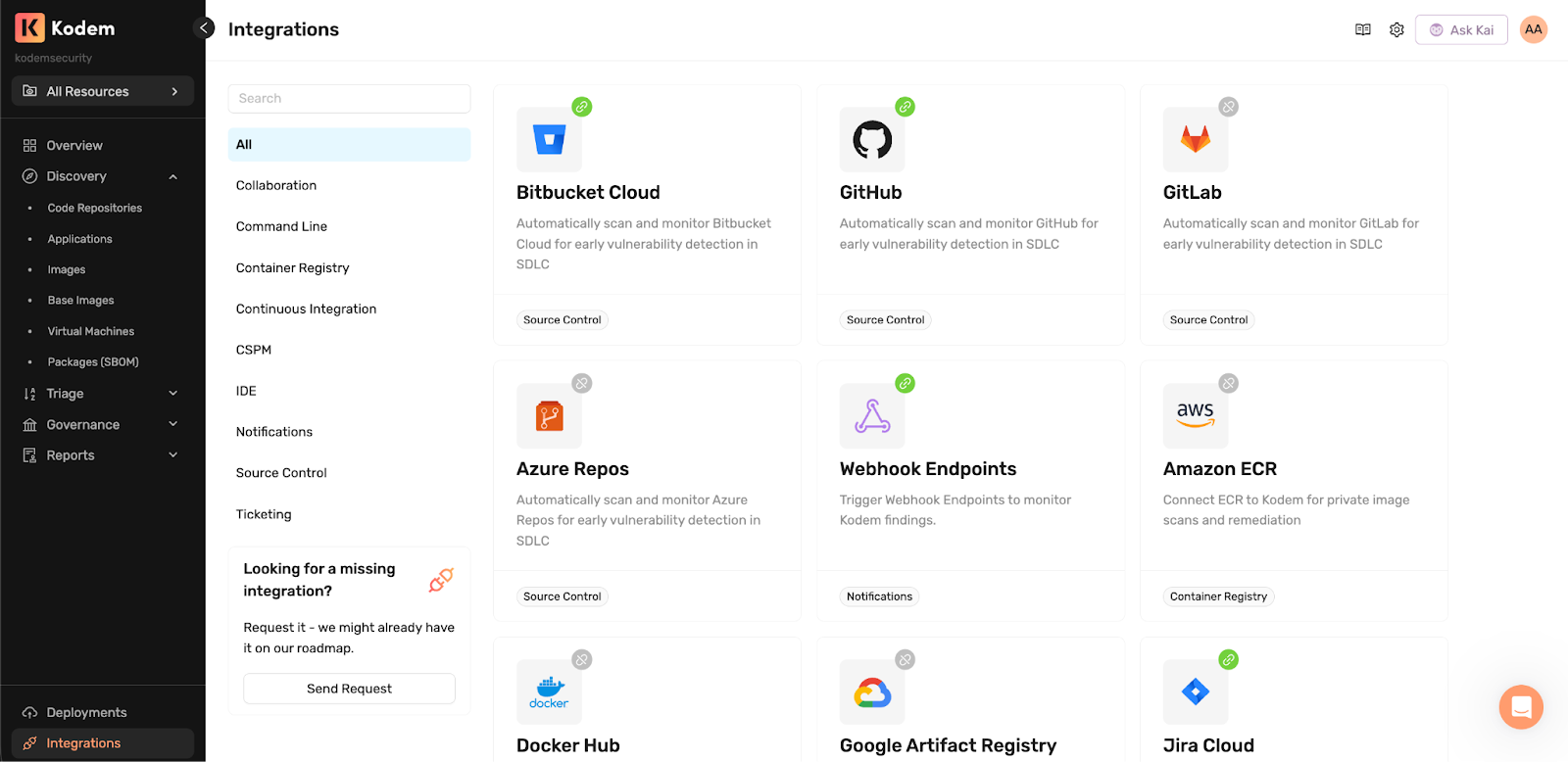
2. Deploy runtime sensors
To ground findings in real execution context, teams deploy Kodem’s lightweight runtime sensors into the environments that matter.
Supported environments include:
- Kubernetes, including GKE, GKE Autopilot, AKS, EKS.
- ECS or ECS Fargate.
- Serverless and VM-based deployments.
Sensors are deployed using guided Helm or CloudFormation workflows designed to minimize operational overhead. Most teams start with a small pilot deployment to validate coverage, then expand gradually as needed. Meaningful findings typically begin populating within hours, rather than weeks or months.
Together, source code connectivity and runtime sensors provide immediate, evidence-backed visibility, without requiring code changes, invasive instrumentation, or extensive upfront configuration.
3. Integrate only what you need
Once visibility is established, teams selectively add what they need:
- Container registry integrations.
- CI policy enforcement.
- SCM policies.
- Jira ticketing.
- SSO / SAML authentication.
- Role-based access controls.
The Real Benefit: Less Waste, Faster Trust
When visibility comes first:
- Teams don’t over-integrate.
- Data is trusted earlier because it reflects reality, not theory.
- Developers engage sooner because findings are relevant and explainable.
- Security teams focus on impact rather than volume.
True AppSec implementation goes beyond deployment. Rather than spending months wiring a platform that may or may not deliver value, effective teams gain clarity first and let that understanding shape everything that follows.
Related blogs
.png)
From SBOM Inventory to Package Intelligence
How Kodem turns SBOM packages into the control plane for investigation, governance and remediation

Kai at Work: A Day in the Life of an AI AppSec Engineer
Kai, Kodem’s secure-by-design AI AppSec Engineer, is integrated directly into the platform to deliver contextualized and actionable answers precisely when AppSec teams need them. By converting your existing security data into conversational intelligence, Kai eliminates the need for hours of manual investigation and context-switching. You can now ask questions as you would to a senior, humble, and tireless engineer.

Remediation That Meets Developers in Context
Identifying issues isn’t the challenge. The challenge is effective remediation that fits your codebase, your environment and your team’s development velocity. Developers need to understand where issues originated, which packages to upgrade, what code to change and how disruptive fixes will be. Meanwhile, AppSec needs visibility into what's immediately actionable and which issues require cross-team coordination.
A Primer on Runtime Intelligence
See how Kodem's cutting-edge sensor technology revolutionizes application monitoring at the kernel level.
Platform Overview Video
Watch our short platform overview video to see how Kodem discovers real security risks in your code at runtime.
The State of the Application Security Workflow
This report aims to equip readers with actionable insights that can help future-proof their security programs. Kodem, the publisher of this report, purpose built a platform that bridges these gaps by unifying shift-left strategies with runtime monitoring and protection.
.png)
Get real-time insights across the full stack…code, containers, OS, and memory
Watch how Kodem’s runtime security platform detects and blocks attacks before they cause damage. No guesswork. Just precise, automated protection.




